 |
Getting to the Root of Software Security Vendors try to protect their source code from would-be attackers, but it takes only one chink in the armor for a good reverse engineer to penetrate all the defenses so carefully put in place. Find out how to methodically uncover patterns to help you predict where the attacks will be focused and how they will be carried out.
|
|
|
|
Domain-Centric Programming: Redefining the Universe Sometimes to build better software you have to challenge long-standing assumptions. Find out what happened when one programmer realized his priorities were upside-down.
|
|
 |
An Elephant in the Room We make software so that people can use it. Yet these users are so hard to define that they are often simply ignored. This six-step approach to Interaction Design can help you bring your customers down to size so that you can provide the right product for them.
|
|
 |
Not a Game of Random() Chance Online gaming poses a myriad of security risks. These hazards include various forms of player cheating and the possibility of unfair gaming software, in addition to the risks normally associated with any e-commerce business. Matthew Schmid describes a specific design flaw in an online poker game.
|
|
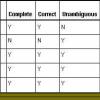 |
On-Track Requirements: How to Evaluate Requirements for Testability Prior to using the requirements to develop the Test Plan, an analysis should be performed to evaluate the testability of the requirements. This article suggests a proven method used on a recent project that accomplishes such an evaluation.
|
|
Pages
Visit Our Other Communities
AgileConnection is a TechWell community.
Through conferences, training, consulting, and online resources, TechWell helps you develop and deliver great software every day.

