|
|
Who do You Trust? The defensive programmer may sometimes feel a touch of paranoia in his work, but it’s all part of the job. Writing code today that is robust and defensive will help protect against the potential errors of the unforeseeable future.
|
|
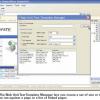 |
A Look at GreenBlue Inspector by Ecyware Why should hackers have all the good tools? Marnie Hutcheson takes a look at Ecyware's GreenBlue Inspector, an inexpensive tool that automates gray box vulnerability testing for simple data types, buffer overflow, SQL injection, and cross-site scripting in forms, cookies, and client requests.
|
|
 |
A Critical Line of Defense Tackle software vulnerabilities at the root—in the applications themselves.
|
|
 |
What's the Buzz Need information but don’t have time to wade through bookracks looking for that perfect reference? The StickyMinds.com Books Guide can help. Get the scoop from StickyMinds.com members on three books that can keep you up to date on the latest issues.
|
|
|
|
The Enemy Within Not all threats come from outsiders. In an era of downsizing, layoffs, and pay cuts, sometimes it's your own disgruntled employees (or ex-employees) who are targeting you. Get some tips to help you protect your software from sabotage.
|
|
|
|
Damage Control Turn to The Last Word, where software professionals who care about quality give you their opinions on hot topics. This month, read why perhaps software should come equipped with seat belts and an air bag.
|
|
|
|
A Killer Bug for the New Millenium We're pleased to bring you technical editors who are well respected in their fields. Get their take on everything that relates to the industry, technically speaking. In this issue, find out why our guest editor thinks he's found the bug that will once again bring testers to the forefront—a bug that dwarfs Y2K and could put big, rich software companies out of business.
|
|
|
|
Case Your Own Joint Hackers are going to probe your system looking for weak spots and holes. What will they find? Learn how to uncover your own security vulnerabilities before the bad guys do.
|
|
 |
Warning: Security Storm Brewing For too long now, consumers have been bailing, patching, and plugging their software each time a new security hole is discovered. And they've been absorbing the damage done by the leaks. A wave of security-conscious buyers is rising, demanding software that is sound and secure by design. Are you ready to give it to them? Find out why you should be.
|
|
|
|
Security Testing by Steven Splaine For anyone involved in security testing, or for anyone who is just plain curious about this area of software testing, the following references will provide a good starting point for any effort that you might be asked to undertake. In this issue, Steven Splaine discusses this important aspect of software engineering.
|
|

